Note: In this blog, we have discussed key features of Nagios Core (the free version), and not Nagios XI (the paid version of Nagios).
Let us start with the basics before getting into the key differences.
Understand Security Testing?
“Security means allowing authorized access to protected data and restricting unauthorized access.”
Security testing is a non-functional testing procedure. It ensures that the data has the necessary protection and security. Also only authorized users can access the system and that no information is leaked. We employ a variety of software, hardware, and firewalls, including metaspoilt, Wireshark, w3af, netsparker, ZED attack proxy (ZAP), and others.
Why do we perform Security testing?
It determines if the software is subject to cyber threats and how malicious or unexpected inputs affect its operation. It verifies that systems and data are secure and trustworthy and that unauthorized inputs are not accepted.
There are two main purposes of Security testing.
⦁ Finding system vulnerabilities before the attacker does, and
⦁ Determining if changes to the system mistakenly created new vulnerabilities.
ZAP TOOL
To create a secure online application, you must first understand the pattern of attacks. Here comes the need Security Testing, also known as penetration testing.
Companies utilize pricey tools for security objectives. The best part about ZAP that makes Penetration Testing easier for testers.
ZAP application security testing is the security testing tool which is used for performing Security testing for maiking software secured. ZAP Security Testing tool was invented by Simon Bennetts in 2010 and maintained by Open Web Application Security Project(OWASP).
Yeap, It is open-source tool!
This security testing tool is one of the most popular open-source dynamic application security testing tools. It is maintained by OWASP and has a huge community that creates new features and add-ons, making it very versatile. The basic purpose of Zap is to simplify penetration testing for Digital applications as simply as possible.
Advantages of ZAP
- Zap is cross-platform, which means it works on all operating systems (Linux, Mac, Windows)
- It is for Digital Applications
- You can reuse Zap.
- Can provide reports
- Beginner-friendly
- Free software
How Does ZAP Serve?
OWASP ZAP penetration security testing tool sets up a proxy server and routes all website traffic through it. The implementation of auto scanners in ZAP facilitates the detection of website vulnerabilities.
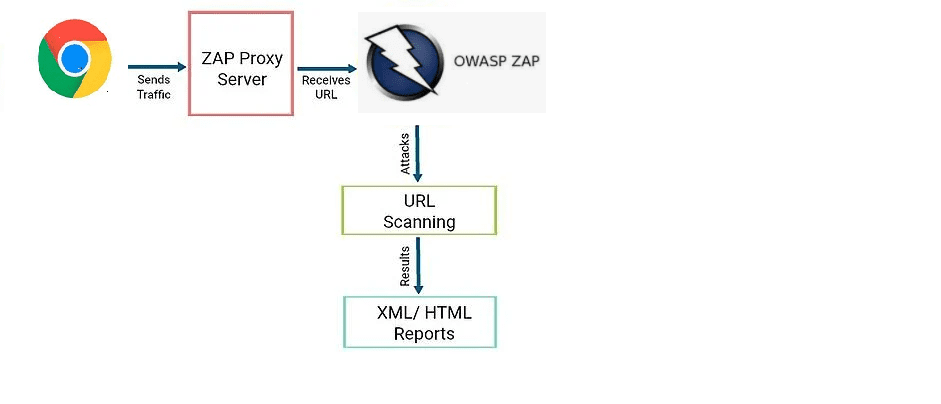
Scan the web application by ZAP and identify problems with following:
Injection of SQL
Authentication Trouble
Revealed
sensitive data
Access control is flawed.
Misconfiguration of security
Site-to-Site Scripting (XSS)
Deserialization using Insecurity
Vulnerabilities in known
components
Security headers are missing
7 Advantages of Using ZAP Tool For Security
Testing
There are the following 7 perks for choosing ZAP:
Jenkins Plugin
Integrating DAST tools into a CI/CD pipeline management like Jenkins is becoming increasingly prevalent as more firms move towards DevSecOps or Agile security testing approaches. Need plugin for such integrations.
Need to include the security testing in the CI/CD process which is done by Jenkins Plugin. We’ve helped our customers incorporate ZAP easily into the DevOps pipeline using the Jenkins plugin, allowing teams to execute automatic scans per release. Several ZAP pipeline functions are enabled by the plugin. Including Spider Scans, AJAX Spidering, Active Scan, Managing Sessions, Defining Context, and correlating results.

Fuzzing
With fuzzing, we can change the response from a web application. And see the results in real-time.
A fuzzer is a security tool that injects various payloads into an application to make it go to an undesired state, potentially exposing a vulnerability. In ZAP, testers can choose from a range of open-source fuzzing payload lists. It is through sources like Dirbuster, FuzzDB, and JbroFuzz. You can unearth vulnerabilities easily with Zap building it.
ZAP provides fuzzing capabilities to send incorrect or unexpected data to a tested application. This can help identify security issues. There are many built-in payloads you can choose from. Or you can download payloads from the ZAP community and add-ons. You can also create your own payloads.
Fuzzing is sending unexpected or random data to a website’s inputs.
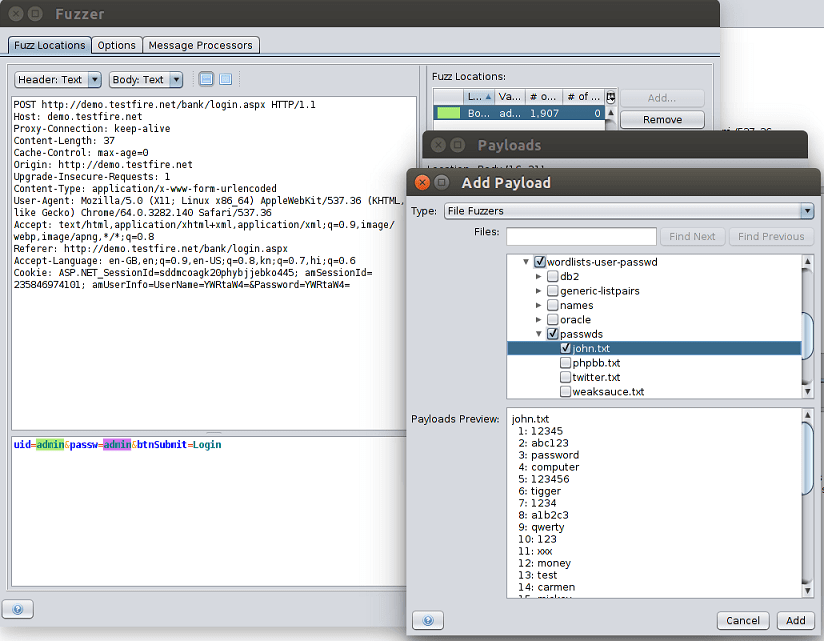
We usually validate inputs on the client-side, which is why we overlook some issues in the backend. You can find coding mistakes and security loopholes. This is done by fuzzing important inputs (such as the website’s main search input or the login page inputs). This is a security measure that is optional. To use Fuzzer, go to the left pane and find the request you wish to fuzz. Select Attack from the context menu, then Fuzz.
The request post data is visible in the Fuzzer window. Select the text you wish to attack from the post data by clicking on it. Click the Add button in the right pane. The Payloads window will appear. Click the Add button once more. Choose File Fuzzers from the Type combo box in the Add Payload dialogue. Choose the appropriate file. This file serves as a database for brute-forcing the input. Fuzzer tab at the bottom shows the results when it finishes. Suspect and avoid those with the Fuzzed tag.

A place for big ideas.
Reimagine organizational performance while delivering a delightful experience through optimized operations.


Ajax Spider
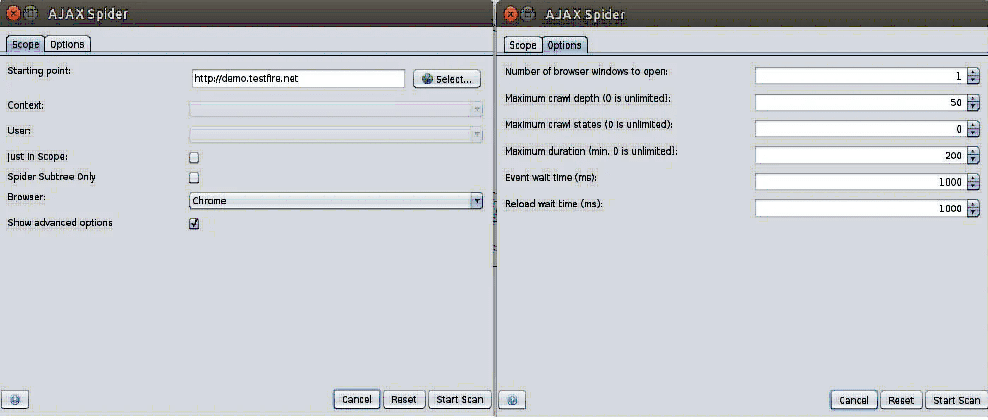
AJAX spidering is a process of discovering requests on an AJAX-rich web app that cannot be found using a regular spidering tool. This can be done by accessing the AJAX spidering window via ZAP -> Tools -> AJAX Spider on ZAP’s menu bar. The tool has various configuration settings, such as maximum depth to crawl, maximum crawl states, maximum duration, and other options to prevent the possibility of infinite crawling.
For our penetration tests, we first use a regular spidering tool to identify the URLs of the application being tested. By running the AJAX spider after the regular spidering, we get a better map of all application resources in scope. With ZAP, you have the option to automatically open the application in a browser using Selenium and explore the application through an event-driven dynamic crawling engine. This eliminates the need for a manual walkthrough of the application to capture AJAX requests.
What is the purpose of spidering?
You don’t need to utilize the spider if you access all areas of the site while exploring your website; it’s there to pick up on anything you missed or when proxying isn’t an option.
You can accomplish it accomplished by right-clicking the site and selecting Attack from the menu, followed by Spider. Be sure to turn on the recurse option! Press the Scan button to begin scanning. It will take some time depending on how many links your website has.

Using the REST API to Interact with ZAP Programmatically
You can communicate with ZAP programmatically using the Application Programming Interface (API) offered by ZAP. In Other words Zap provides API Security Testing Services too.
JSON, HTML, and XML are the three different formats of offering the API. When using ZAP, you may access a simple web UI that allows you to explore and use the API by visiting http://zap/ or by visiting the host and port ZAP is listening on, for example, http://localhost:8080/.
By default, only the system on which ZAP is operating has access to the API. You can give access to the API to other machines that can use ZAP as a proxy. To set up the API it uses the options API screen. Most of the key ZAP capabilities, such as the active scanner and spider, are accessible via the API.
Script-friendly
Scripts can automate many aspects of application security testing with , saving time and allowing the tester to focus on other critical duties.
ZAP is one of the most scripting utilities available, supporting any JSR 223 scripting language. Through the ZAP Script Add-on, ZAP can run scripts that can be inserted within it to access internal data structures and features. Javascript, Zest, Python, Groovy, and Ruby are among the scripting languages supported.
It supports Stand-alone, Active Rules, Proxy Rules, and other scripts. We leveraged ZAP’s “record scripts” capability to develop Zest scripts. This do automatic walkthroughs of an application, proxy the requests through ZAP, run scans, and export the data for further aggregation and correlation.
Flexible Policy Management for Scan
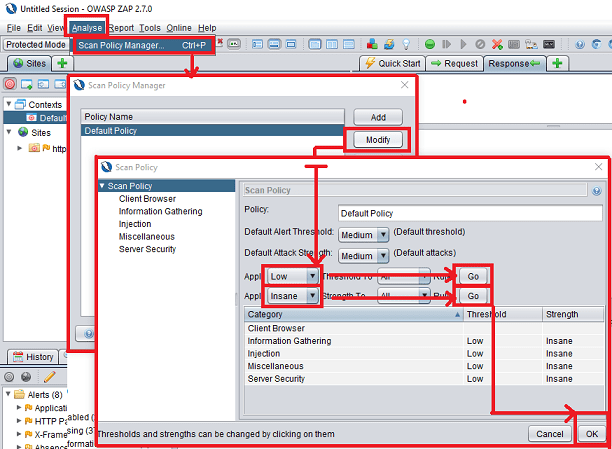
ZAP gives you the freedom to create a scan policy for any application based on the tester’s needs. You can find the Scan Policy Manager in the menu bar under Analyze>>Scan Policy Manager.
It is critical for a pen-tester to optimize the scanner focus on the target application’s ability to keep up with its operational performance (and not result in a DoS). When creating scan policies, it’s vital to think about a scanner’s processing and bandwidth capabilities.
Anybody can change the scan policy to include or exclude specific types of tests changes. You can even customize the definition of factors like Threshold and Strength.
There is a requirement of Pen-testers to test scenarios that they may encounter on a regular basis in target apps. You can create a custom scan policy in ZAP and export it as a template. Zap can reuse and import this scan policy.
Configure SCAN Policy
Select Scan Policy Manager from the Analyze menu. Select the Modify button. Set Low => Threshold To All in the Scan Policy screen, then click the Go button. Similar to Insane => Strength To All and then press the Go button. To save, click the OK button. This eliminates all attacks in memory and strengthens the scan.

WebSockets
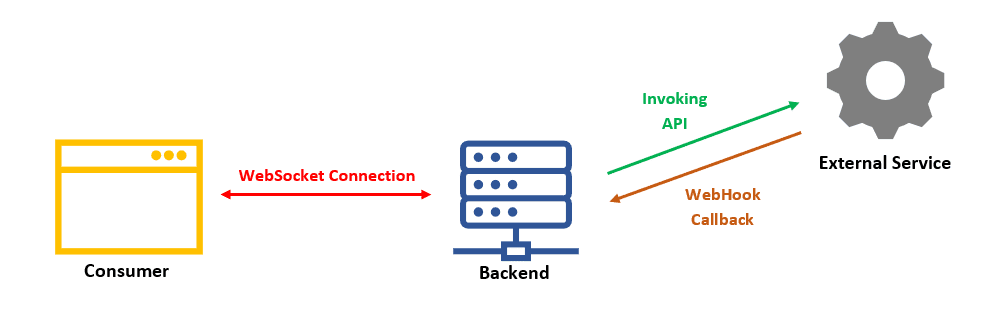
WebSockets allow web applications and websites to build a bi-directional (two-way) full-duplex communication channel over a single TCP connection.
ZAP Likewise list each message’s opcode – Text, Binary, Close, Ping, or Pong. For further examination, based on opcodes or channels you can filter the messages. The fuzzer can also retrieve the WebSocket message for subsequent payload insertion.
It has following abilities:
ZAP intercept and display messages.
Breakpoints are set by ZAP for specific types of WebSocket messages.
Fuzzes them (send lots of invalid or unexpected data to a browser or server).
It has programs to passively check WebSocket messages and raise alerts.

To sum up, OWASP ZAP penetration security testing tool is a free and powerful security solution. It is simple to install and configure. Therefore we may use it upfront to secure our online application. And monitor all kinds of security risks. Further it allows us to create a safe online application.
For instance the ZAP tool is a useful tool that comes in handy while developing and testing web applications. As we’ve seen, some problems might be so deep within an application that utilizing a tool like ZAP is the only way to find them. This program combines the capabilities of automatic scans with the ability for the tester to manually filter through pages and tamper with requests.
“Testing is not responsible for the bugs inserted into software any more than the sun is responsible for creating dust in the air.”— Dorothy Graha
- Understand Security Testing?
-
- 7 Advantages of Using ZAP Tool For Security
-
Testing
- Jenkins Plugin
- Ajax Spider
- What is the purpose of spidering?
- Using the REST API to Interact with ZAP Programmatically
- Script-friendly
- Flexible Policy Management for Scan
- Configure SCAN Policy
- WebSockets
- It has following abilities:
- “Testing is not responsible for the bugs inserted into software any more than the sun is responsible for creating dust in the air.”— Dorothy Graha